@lyse@lyse.isobeef.org Thanks for sharing. I really enjoyed it. The beginning part about the history of life on Earth was fun to watch having just read Dawkin’s old book The Selfish Geene, and now I want to read more about archaea. The end of the talk about what might be going on on Mars made me a bit hopeful someone will find some good evidence.
Just leaving this book here for no reason 🤫
Skill Issues of course, but that's going away next as soon as I get my php-fpm shi_ together.
@prologic@twtxt.net I’d stumbled upon #FrankenPHP while reading through #Caddy stuff and thought maybe it’s bit overkill for what i need it for but then again, it will be just a “One container in for two out”, that’s win in my book 😆
Nouveau billet intitulé “La trilogie Mars est solarpunk” https://si3t.ch/log/2025-01-25-mars-KSR.txt #solarpunk #book #sf
Lowkey planning out a book (anthology. Maybe) of just playscripts in my Greek myth yuriverse. Thank u lord
@aelaraji@aelaraji.com Reading “The Book Thief” by Markus Zusak
Cancelled Mastodon because the time spent on it could have been used for reading books instead and the level of interaction is not enough to keep me interested.
@prologic@twtxt.net @eapl.me@eapl.me @bender@twtxt.net I just found:
Equilibrium problems are solved by method of relaxation numerically.
– Manoj Kumar and Garima Mishra, https://www.scirp.org/html/8798.html
Reminds me of deliberately misattributed quotes from a funny German book series “Die Känguru-Chroniken”, like:
How much is the fish?
– Karl Marx
I’m positively surprised there is even an English wikipedia page about The Kangaroo Chronicles. Somebody gathered a list with all of them.
@movq@www.uninformativ.de Yeah, the Python docs are more like a book. They absolutely shine if you have no idea and read them from top to bottom. The tutorial is baked right in. But they don’t work all that perfect as cheat sheets. I also remember looking for the return types way too long in the past.
I would have thought that this could be easily improved when type hints are in place. And it sure does: https://www.tornadoweb.org/en/stable/httpclient.html#tornado.httpclient.HTTPClient.fetch
Way to go F*** Book! With another $263M going down the drains … And people’s lives/data with it.
Tab and expected it to auto-complete. 🤦
Brilliant, @movq@www.uninformativ.de, I didn’t think of the keystore! :-D
Me too, @aelaraji@aelaraji.com, I don’t know how many entire books I had to rewrite because of Ctrl+W irreversibly deleting the entire chapter.
An inspiring book on making a life around IT security
Troy Hunt: “Pwned”, The Book, Is Now Available for Free
https://www.troyhunt.com/pwned-the-book-is-now-available-for-free/
The web server in Calibre is pretty cool. Love how the UI was designed and made. Feels intuitive, yet powerful. Now i do need to organise the book collection a bit better.
@prologic@twtxt.net I bet our twts are already being fed to circuit monsters… Remember the other day when I’d snapped out about some nonsense, being an A-Hole and what not? I’ve seen an AI company employee lurking around with not much interaction (if I’m not mistaken), so my mind went on auto-pilot mode thinking “This !#@%$ must be feeding us to the circuit peggy monster!! Arrr 😤” 🤣🤣🤣 but then again, one shouldn’t judge a book by it’s cover (or an employee by his title) right?
If all Orange Face Elefant party voters would take them on their words and make them actually do whatever insane world they invented, then perhaps people will realize the grave mistake that was made today. Many people have to feel consequences before they believe it. I hope there will still be history books in the future to disclose the insanity for future generations. But whatever happens, the World will keep spinning…
i’m so glad i gave up christianity. i might be a little less glad when i get purged, but at least i won’t be doing the purging. jesus of nazareth has some chill teachings, but the whole thing is poisoned by the actual history of the religion. genocide, book burnings, and ethnic cleansing are not exactly noble teachings.
Inversion by Aric McBay was another random library pick. Like The Fall of Io, it’s the most recent in a series, though I think this series is pretty loosely connected. In contrast, the villain in this book is simple and cartoonishly evil. The book presents a design for utopia which was interesting but a little cloying. I’m not sure if I’m supposed to want to live there, but I don’t think I do. I enjoyed the book as easy reading, and might try the others in the series some time. (4/4)
I read Starter Villain by John Scalzi. Enjoyable, like his other books that I’ve read. Somewhat sillier. (¾)
Lol, this is actually a good thing by Apple. Doesn’t kill social apps at all, just prevents some harvesting of your entire address book by abusive apps like WhatsApp.
Did Apple Just Kill Social Apps?
Apple’s iOS 18 update has introduced changes to contact sharing that could significantly impact social app developers. The new feature allows users to selectively share contacts with apps, rather than granting access to their entire address book. While Apple touts this as a privacy enhancement, developers warn it may hinder the growth of new social platforms. Nikita Bier, a start-up founder, called it “the en … ⌘ Read more
@bender@twtxt.net It’s the experience of an ordinary person in a strange place where memories are disappearing with the help of the Memory Police. The setting feels contemporary (to the book’s 1994 publication date) rather than futuristic, except for some unexplained stuff about memories.
Recent #fiction #scifi #reading:
The Memory Police by Yōko Ogawa. Lovely writing. Very understated; reminded me of Kazuo Ishiguro. Sort of like Nineteen Eighty-Four but not. (I first heard it recommended in comparison to that work.)
Subcutanean by Aaron Reed; https://subcutanean.textories.com/ . Every copy of the book is different, which is a cool idea. I read two of them (one from the library, actually not different from the other printed copies, and one personalized e-book). I don’t read much horror so managed to be a little creeped out by it, which was fun.
The Wind from Nowhere, a 1962 novel by J. G. Ballard. A random pick from the sci-fi section; I think I picked it up because it made me imagine some weird 4-dimensional effect (“from nowhere” meaning not in a normal direction) but actually (spoiler) it was just about a lot of wind for no reason. The book was moderately entertaining but there was nothing special about it.
Currently reading Scale by Greg Egan and Inversion by Aric McBay.
Book of Shadows - Sacred-Texts | https://sacred-texts.com/bos/index.htm
If some of you budding fathers want to know how I created a computer nerd to one day work for Facebook in the big USA, well you purchase a $1000 Xmas present, an enormous thick book with C++ programming, and say, you can play as many games as you like kids, but James has to create them using computer software.
SO James created once a 3D chess program with sound, took 6 months or so, really hard to beat, not based on logic moves point by point like other chess programs, this one was based on the depth of looking for patterns, set it to 5 moves ahead and you were toast every time. Nice program too, sadly gone over the years, computers suffer from bit rot. We used to try and mark rotten hard drive discs once as bad sectors, not sure how UBuntu does this these days, I see a dozen errors on the screen every time I load.
Today I would purchase for my kids AI CAD simulation software with metal 3D printer and get your child to build fancy 3D models and engines from scratch. This will make them an expert in the CAD AI industry by the time they are 14 years old. Sadly AI is here to stay and will spoil the Internet.
Thank “Human Goodness” for the Gutenberg Project and all the books I’ll get to immerse myself into, especially in such hard times 🙏
I’ve been thinking about a new term I’ve come across whilst reading a book. It’s called “Complexity Budget” and I think it has relevant in lots of difficult fields. I specifically think it has a lot of relevant in the Software Industry and organizations in this field. When doing further research on this concept, I was only able find talks on complexity budget in the context of medical care, especially phychiratistic care. In this talk it was describe as, complexity:
- Complexity is confusing
- Complexity is costly
- Complexity kills
When we think of “complexity” in terms of software and software development, we have a sort-of intuitive about this right? We know when software has become too complex. We know when an organization has grown in complexity, or even a system. So we have a good intuition of the concept already.
My question to y’all is; how can we concretely think about “Complexity Budget” and define it in terms that can be leveraged and used to control the complexity of software dns ystems?
Picked up Altered Carbon again on Netflix. Really need to read those books.
The last time I did so, I ended up injuring my neck reading an old stash of books we’ve had laying around at home. It took months to heal. xD
UDF is where its at. Not some silly red or blue book that cant even have more than 8+3 filenames!
More basement:
I completely forgot that DVD-RAM was a thing once. Found my old disks and they still work. 🤯 The data on them is from 2008, so they’re not that old. Still impressive.
The disks are two-sided. On the photo, that particular side of the disk on the left appears to be completely unused. 🤔
And then I read on Wikipedia that DVD-RAMs aren’t produced anymore at all today. Huh.
(I refuse to tag this as “retrocomputing”. Read/write DVDs that you can use just like a harddisk, thanks to UDF, are still “new and fancy” in my book. 😂)
All #dune to read and enjoy original story: https://archive.org/details/frank-herberts-dune-saga-collection-books-1-6-by-frank-herbert
Asked an “AI Assistant” (Perplexity) to summarize my introduction of my homepage and then I asked it to give me some book recommendations I might like, and the thing actually nailed it.
Update on my Fibre to the Premise upgrade (FTTP). NBN installer came out last week to install the NTD and Utility box, after some umming and arring, we figured out the best place to install it. However this mean he wasn’t able to look it up to the Fibre in the pit, and required a 2nd team to come up and trench a new trench and conduit and use that to feed Fibre from the pit to the utility box.
I rang up my ISP to find out when this 2nd team was booked, only to discover to my horror and the horror of my ISP that this was booked a month out on the 2rd Feb 2024! 😱
After a nice small note from my provider to NBN, suddenly I get a phone call and message from an NBN team that do trenching to say it would be done on Saturday (today). That got completed today (despite the heavy rain).
Now all that’s left is a final NBN tech to come and hook the two fibre pieces together and “light it up”! 🥳
@xuu@txt.sour.is Despite that these AoC math text problems are rather silly in my opinion (reminds me of an exercise in our math book where somebody wanted to carry a railroad rail around an L-shaped corner in the house and the question was how long that rail could be so that it still fits — sure, we’ve all carried several meter long railroad rails in our houses by ourselves numerous times…), these algorithms are really neat!
The best gift anyone could give me is the time to be able to finish reading some books.
On the book wishlist: https://solar.lowtechmagazine.com/2023/10/thematic-book-series-how-to-downsize-a-transport-network/
Book Podcasts
 ⌘ Read more
⌘ Read more
@New_scientist@feeds.twtxt.net because of course they have.
Emily Bender, a computational linguistic and excellent critic of this generative AI nonsense, uses an analogy of an oil spill to characterize what is happening as a result of generative AI. It’s polluting the world with false information, false images, false “academic” articles, false books. The companies that create this stuff are not cleaning up their misinformation spill; they’re letting the mess spread all over. It’s being used to commit crimes, and that’ll only get worse. Just like an out of control oil spill will destroy entire ecosystems.
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.
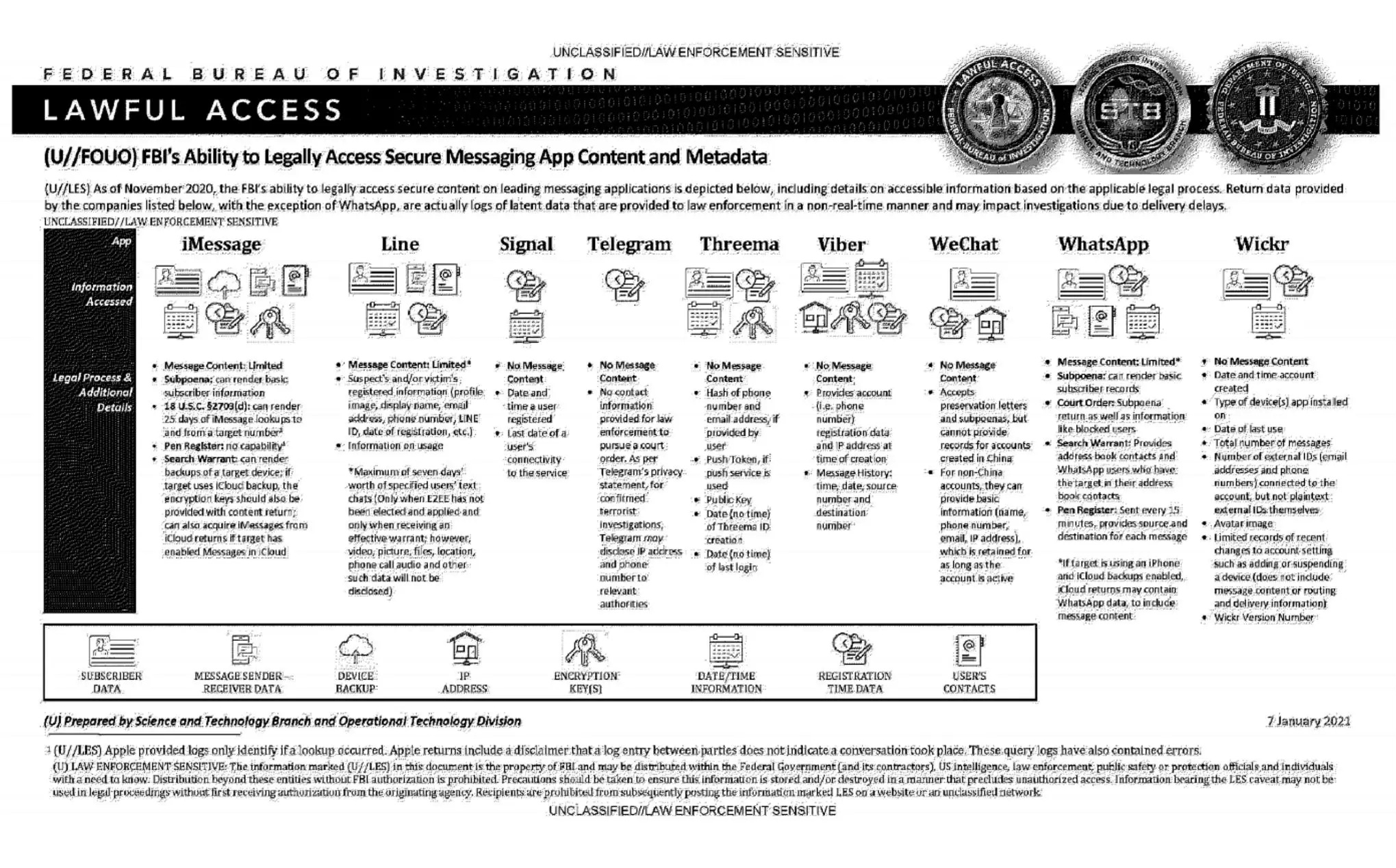
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
Speaking of men getting owned, Ruth Ben-Ghiat, an expert on authoritarianism who wrote the book Strongmen, regularly calls out and degrades wannabe dictators like Elon Musk and it’s cathartic to witness.
@movq@www.uninformativ.de I was visiting Germany once, and saw a guy try to load his bicycle onto the bike racks they have on the front of city buses. There were rules about when you could do that, which were posted on the bus stop sign, and I guess the guy thought this was a time when he could do that. But no, the bus driver disagreed. The bus driver got off the bus with a rule book, flipped it open to what I guess were the rules about bikes on the bus, and showed him the rules. The guy pointed at the sign, the bus driver said no and pointed at the book, and they went back and forth for I don’t know how long. It felt a lot like these videos lol
Omniknot
 ⌘ Read more
⌘ Read more
Alright, check this out. I just kinda completed today’s project of converting a jeans into a saw bag. It’s not fully done, the side seams on the flap need some more hand sewing, that’s for sure. No, I don’t have a sewing machine. Yet?

At first I wanted to put in the saw on the short side, but that would have made for more sewing work and increased material consumption. As a Swabian my genes force me to be very thrifty. Slipping in on the long side had the benefit of using the bottom trouser leg without any modification at all. The leg tapers slightly and gets wider and wider the more up you go. At the bottom it’s not as extreme as at the top.
The bag is made of two layers of cloth for extra durability. The double layers help to hide the inner two metal snap fastener counter parts, so the saw blade doesn’t get scratched. Not a big concern, but why not doing it, literally no added efforts were needed. Also I reckon it cuts off the metal on metal clinking sounds.
The only downside I noticed right after I pressed in the receiving ends of the snap fasteners is that the flap overhangs the bag by quite a lot. I fear that’s not really user-friendly. Oh well. Maybe I will fold it shorter and sew it on. Let’s see. The main purpose is to keep the folding saw closed, it only locks in two open positions.
Two buttons would have done the trick, with three I went a bit overkill. In fact the one in the middle is nearly sufficient. Not quite, but very close. But overkill is a bit my motto. The sides making up the bag are sewed together with like five stitch rows. As said in the introduction, the flap on the hand needs some more love.
Oh, and if I had made it in a vertical orientation I would have had the bonus of adding a belt loop and carrying it right along me. In the horizontal layout that’s not possible at all. The jeans cloth is too flimsy, the saw will immediately fall out if I open the middle button. It’s not ridgid enough. Anyways, I call it a success in my books so far. Definitely had some fun.
I would HIGHLY recommend reading up on the keybase architecture. They designed device key system for real time chat that is e2e secure. https://book.keybase.io/security
A property of ec keys is deriving new keys that can be determined to be “on curve.” bitcoin has some BIPs that derive single use keys for every transaction connected to a wallet. And be derived as either public or private chains. https://qvault.io/security/bip-32-watch-only-wallets/
I’m doing this thing again where I am collecting more articles and books to read than actual doing any reading.
The Weaving The Web Book by Tim Berners-Lee should be a required read for anyone building on the Web.
Decided to keep the smart-phone out of our bedroom and keep a note book instead. Already feeling lighter and fresher.
i’ve been meaning to read these notes, maybe putting the book on my ereader will be a better reminder than whatever i did last time 😅

