#fzf is the new emacs: a tool with a simple purpose that has evolved to include an #email client. https://sr.ht/~rakoo/omail/
I’m being a little silly, of course. fzf doesn’t actually check your email, but it appears to be basically the whole user interface for that mail program, with #mblaze wrangling the emails.
I’ve been thinking about how I handle my email, and am tempted to make something similar. (When I originally saw this linked the author was presenting it as an example tweaked to their own needs, encouraging people to make their own.)
This approach could surely also be combined with #jenny, taking the place of (neo)mutt. For example mblaze’s mthread tool presents a threaded discussion with indentation.
@xuu@txt.sour.is I think it is more tricky than that.
“A company or entity …”
Also, as I understand it, “personal or household activity” (as you called it) is rather strict: An example could be you uploading photos to a webspace behind HTTP basic auth and sending that link to a friend. So, yes, a webserver is involved and you process your friend’s data (e.g., when did he access your files), but it’s just between you and him. But if you were to publish these photos publicly on a webserver that anyone can access, then it’s a different story – even though you could say that “this is just my personal hobby, not related to any job or money”.
If you operate a public Yarn pod and if you accept registrations from other users, then I’m pretty sure the GDPR applies. 🤔 You process personal data and you don’t really know these people. It’s not a personal/private thing anymore.
I’m bad with faces, I know that. But I’m having a really hard time recognizing Linus in this video:
https://www.youtube.com/watch?v=4WCTGycBceg
Basically a different person to me. Is it just me or has he really changed that much? 😳
i feel like we should isolate a subset of markdown that makes sense and built it into lextwt. it already has support for links and images. maybe basic formatting bold, italic. possibly block quote and bullet lists. no tables or footnotes
@prologic@twtxt.net the basic idea was to stem the hash.. so you have a hash abcdef0123456789... any sub string of that hash after the first 6 will match. so abcdef, abcdef012, abcdef0123456 all match the same. on the case of a collision i think we decided on matching the newest since we archive off older threads anyway. the third rule was about growing the minimum hash size after some threshold of collisions were detected.
So.. basically a rehash of the email “unsend” requests? What if i was to make a (delete: 5vbi2ea) .. would it delete someone elses twt?
So yeah no, whilst it technically works, neither jenny nor yarnd support it very well. Only at a very basic level.
# follow_notify = gemini://foo/bar to your feed’s metadata, so that clients who follow you can ping that URL every now and then? How would you even notice that, do you regularly read your gemini logs? 🤔
@movq@www.uninformativ.de Damn! I’m two years late to the discussion 😅 So basically, one could just make a bash script/cron job on the side for pinging non-Http feeds from time to time and the receiving end would get it IF they check their logs.
So this is a great thread. I have been thinking about this too.. and what if we are coming at it from the wrong direction? Identity being tied to a given URL has always been a pain point. If i get a new URL its almost as if i have a new identity because not only am I serving at a new location but all my previous communications are broken because the hashes are all wrong.
What if instead we used this idea of signatures to thread the URLs together into one identity? We keep the URL to Hash in place. Changing that now is basically a no go. But we can create a signature chain that can link identities together. So if i move to a new URL i update the chain hosted by my primary identity to include the new URL. If i have an archived feed that the old URL is now dead, we can point to where it is now hosted and use the current convention of hashing based on the first url:
The signature chain can also be used to rotate to new keys over time. Just sign in a new key or revoke an old one. The prior signatures remain valid within the scope of time the signatures were made and the keys were active.
The signature file can be hosted anywhere as long as it can be fetched by a reasonable protocol. So say we could use a webfinger that directs to the signature file? you have an identity like frank@beans.co that will discover a feed at some URL and a signature chain at another URL. Maybe even include the most recent signing key?
From there the client can auto discover old feeds to link them together into one complete timeline. And the signatures can validate that its all correct.
I like the idea of maybe putting the chain in the feed preamble and keeping the single self contained file.. but wonder if that would cause lots of clutter? The signature chain would be something like a log with what is changing (new key, revoke, add url) and a signature of the change + the previous signature.
# chain: ADDKEY kex14zwrx68cfkg28kjdstvcw4pslazwtgyeueqlg6z7y3f85h29crjsgfmu0w
# sig: BEGIN SALTPACK SIGNED MESSAGE. ...
# chain: ADDURL https://txt.sour.is/user/xuu
# sig: BEGIN SALTPACK SIGNED MESSAGE. ...
# chain: REVKEY kex14zwrx68cfkg28kjdstvcw4pslazwtgyeueqlg6z7y3f85h29crjsgfmu0w
# sig: ...
@cuaxolotl@sunshinegardens.org Ah, thanks for reporting back! Okay, so you’re basically manually “crawling” feeds right now. 🤔 What do you think about the idea of adding something like # follow_notify = gemini://foo/bar to your feed’s metadata, so that clients who follow you can ping that URL every now and then? How would you even notice that, do you regularly read your gemini logs? 🤔
@aelaraji@aelaraji.com Ahh it might very well be a Clownflare thing as @lyse@lyse.isobeef.org eluded to 🤣 One of these days I’m going to get off Clownflare myself, when I do I’ll share it with you. My idea is to basically have a cheap VPS like @eldersnake@we.loveprivacy.club has and use Wireguard to tunnel out. The VPS becomes the Reverse Proxy that faces the internet. My home network then has in inbound whatsoever.
@bender@twtxt.net haha funny! though i just realized my ISP is the only one with fiber pulled to the property so i would have to get a phone line from them some how. The other ISP in the area is basically a mobile hotspot.
receieveFile())? 🤔
he emailed my ISP about causing logging abuse. This is the only real ISP in my area, its gonna basically send me back to dialup.
@prologic@twtxt.net Hitting that URL returns a bunch of HTML even though there is no user named lovetocode999 on my pod. I think it should 404, and maybe with a delay, to discourage whatever this abuse is. Basically this can be used to DDoS a pod by forcing it to generate a hunch of HTML just by doing a bogus GET like this.
@movq@www.uninformativ.de Somewhere or another, I think in a William Byrd talk, I heard it suggested that the best ideas in computer science should fit on an index card (ah yes it’s this one: https://paperswelove.org/2017/video/will-byrd-most-beautiful-program/ ). He was referring to the basic principles of LISP/the lambda calculus, which have sometimes been called the Maxwell’s equations of computer programming (by Alan Kay). Simple, short, elegant, but very densely packed with meaning–generations of people have spent their whole careers unpacking what those simple rules can do.
Much of modern software feels like the polar opposite of that. Not only can you not write it on an index card, you never will be able to because people who write software don’t seem to aspire to try. I wish more people thought this way though!
Google Chrome will have Gemini LLM built into the browser.
I run Plan 9 on my server and my main home workstation (a raspberry pi). My “daily driver” time is basically split between that and a Mac (excluding time on my phone, i suppose). I think it looks elegant, too. :-)
Been clearing out my pod a bit and blocking unwanted domains that are basically either a) just noise and/or b) are just 1-way (whose authors never reply or are otherwise unaware of the larger ecosystem)
Let me know if y’all have any other candidates you’d like me to add to the blocked domain list?
yarn should define its own federation protocol that extends the basic twtxt in ways that twtxt doesn’t allow. it’s time. and i’ve got ideas!
@lyse@lyse.isobeef.org its a hierarchy key value format. I designed it for the network peering tools i use.. I can grant access to different parts of the tree to other users.. kinda like directory permissions. a basic example of the format is:
@namespace
# multi
# line
# comment
root :value
# example space comment
@namespace.name space-tag
# attribute comments
attribute attr-tag :value for attribute
# attribute with multiple
# lines of values
foo :bar
:bin
:baz
repeated :value1
repeated :value2
each @ starts the definition of a namespace kinda like [name] in ini format. It can have comments that show up before. then each attribute is key :value and can have their own # comment lines.
Values can be multi line.. and also repeated..
the namespaces and values can also have little meta data tags added to them.

the service can define webhooks/mqtt topics to be notified when the configs are updated. That way it can deploy the changes out when they are updated.
@movq@www.uninformativ.de Haha! yeah sounds about like my HS CS program. A math teacher taught visual basic and pascal. and over on the other end of the school we had “electronics” which was a room next to the auto body class where they had a bunch of random computer parts scavenged from the district decommissioned surplus storage.
The advanced class would piece together training kits for the basic class to put together.
Twtxt spec enhancement proposal thread 🧵
Adding attributes to individual twts similar to adding feed attributes in the heading comments.
https://git.mills.io/yarnsocial/go-lextwt/pulls/17
The basic use case would be for multilingual feeds where there is a default language and some twts will be written a different language.
As seen in the wild: https://eapl.mx/twtxt.txt
The attributes are formatted as [key=value]
They can show up in the twt anywhere it is not enclosed by another element such as codeblock or part of a markdown link.
With all M$’s apps being basically fancy web apps, there is no need to actually install any of their legacy applications locally anymore. Since I am online basically 100% of the time this turns my Office experience in a Chromebook like one. No installs, never outdated software. Just a yearly subscription contribution to worry about.
Obligatory Twtxt post: I love how I can simply use a terminal window and some very basic tools (echo, scp, ssh) to publish thoughts, as they pop up, onto the Internet in a structured way, that can be found and perhaps even appreciated.
@prologic@twtxt.net the new product was GPTs. A way to create tailored bots for specific use cases. https://openai.com/blog/introducing-gpts (fun fact: I did an internal hackathon where we made something like this for $work onboarding. And I won a prize!)
The competed project is poe https://quorablog.quora.com/Introducing-creator-monetization-for-Poe which is basically the same idea. Make a AI bot tailored to a specific domain of knowledge. And monitize it.
The timing fits very well as openAI announced it just a few weeks ago.
So now that I have a basic Twtxt form, I can also update my feed even when I am not on my PC.
Anyone else keeping personal .log files updated through basic shell commands?
How Google Authenticator made one company’s network breach much, much worse | Ars Technica
🤦♂
WHY are these big companies treated as though they are the be all and end all of infosec? These are rookie mistakes Google’s making, at scale.
Unfortunately Google employs dark patterns to convince you to sync your MFA codes to the cloud, and our employee had indeed activated this “feature”. If you install Google Authenticator from the app store directly, and follow the suggested instructions, your MFA codes are by default saved to the cloud. If you want to disable it, there isn’t a clear way to “disable syncing to the cloud”, instead there is just a “unlink Google account” option.
Like, never ever put your multi-factor tokens into a single cloud storage location! The whole point of this being “multi” factor is that there is a separate, independent physical factor involved in the authentication process. If the authenticator app on your phone puts the tokens in the cloud, then it reduces the security that comes from having a second factor. This is basic stuff.
Of course, never ever use Google Authenticator. All it does is generate TOTP and HOTP codes, which you can do with any OTP app, preferably an open source one that’s been vetted.
Would anyone pay for like cheap hosting if it only cost you say ~$0.50 USD per month for a basic space to run your website, twtxt feed, yarn pod, whatever? 🤔 Of course we’re talking slices of a server here in terms of memory and cpu, so this would be 10 milliCores of CPU + 64MB of Memory, more than enough to run quite a bit of shit™ 🤣 (especially when you don’t need to run or manage a full OS)
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.
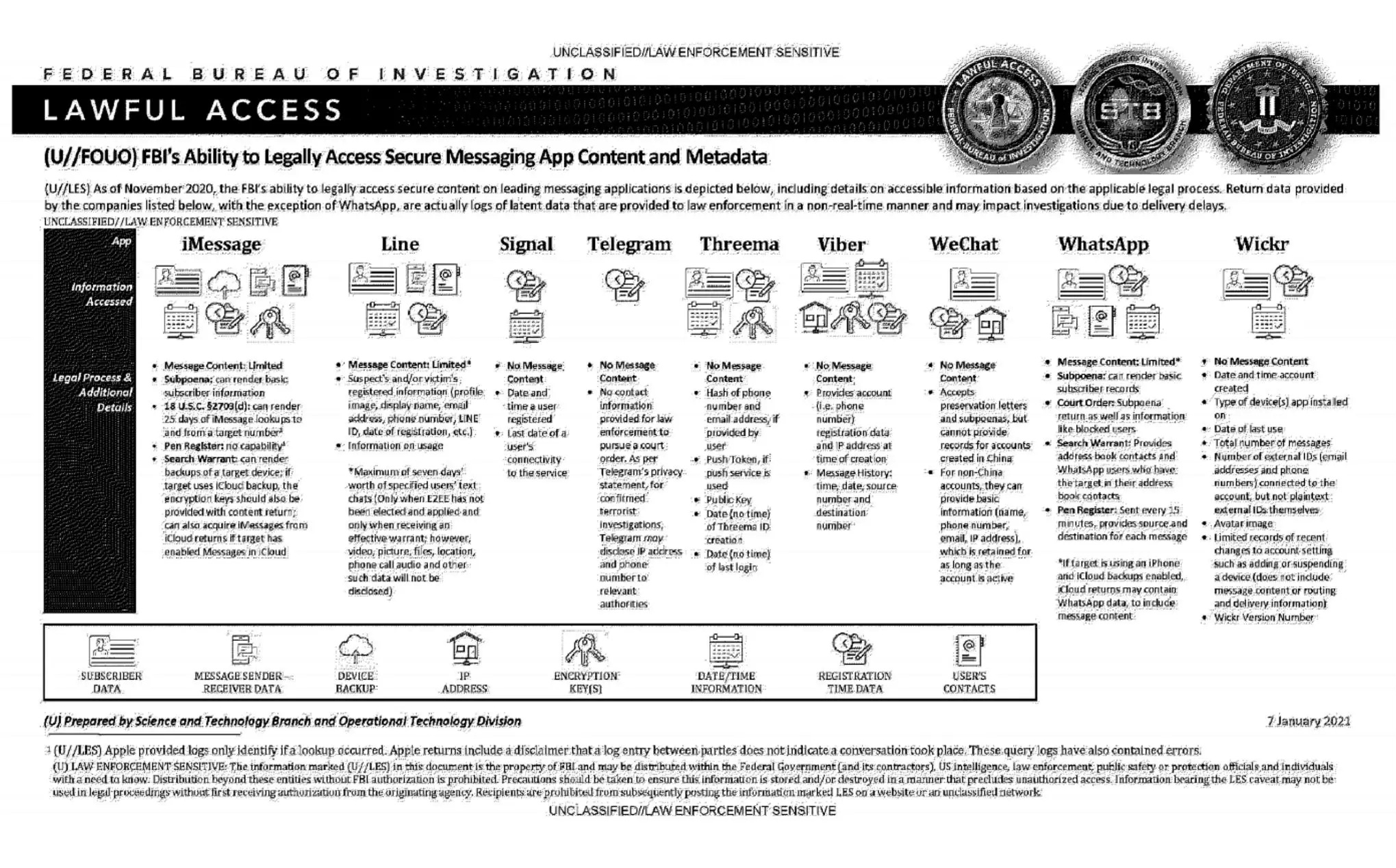
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
@xuu@txt.sour.is Oh wow I didn’t know he was associated with PragerU. I’ve listened to a few episodes of The Audit podcast, where they basically shred PragerU content, and it’s hilarious and terrifying.
@prologic@twtxt.net The hackathon project that I did recently used openai and embedded the response info into the prompt. So basically i would search for the top 3 most relevant search results to feed into the prompt and the AI would summarize to answer their question.
Seems to me you could write a script that:
- Parses a StackOverflow question
- Runs it through an AI text generator
- Posts the output as a post on StackOverflow
and basically pollute the entire information ecosystem there in a matter of a few months? How long before some malicious actor does this? Maybe it’s being done already 🤷
What an asinine, short-sighted decision. An astonishing number of companies are actively reducing headcount because their executives believe they can use this newfangled AI stuff to replace people. But, like the dot com boom and subsequent bust, many of the companies going this direction are going to face serious problems when the hypefest dies down and the reality of what this tech can and can’t do sinks in.
We really, really need to stop trusting important stuff to corporations. They are not tooled to last.
What is a good device for home virtualization these days? I have been looking at the Intel NUC 13 pro’s. Basically I want something “quiet” (ie not a screaming banshee 1U), smallish, but with lots of threads and rams. Disk will come from an external NAS.
BlueSky is cosplaying decentralization
I say “ostensibly decentralized”, because BlueSky’s (henceforth referred to as “BS” here) decentralization is a similar kind of decentralization as with cryptocurrencies: sure, you can run your own node (in BS case: “personal data servers”), but that does not give you basically any meaningful agency in the system.
I don’t know why anyone would want to use this crap. It’s the same old same old and it’ll end up the same old way.
twtxt, as I believe it was originally intended, are short little status updates – that’s it.
So, basically a .plan file for finger. But, on the web. like a *web*finger. We have come full circle on this loop!
We could ask them? But on the counter would bukket or jan6 follow the pure twtxt feeds? Probably not either way… We could use content negotiation as well. text/plain for basic and text/yarn for enhanced.
From my small experience in writing an event database, I am inclined to agree with this.
I played around with parsers. This time I experimented with parser combinators for twt message text tokenization. Basically, extract mentions, subjects, URLs, media and regular text. It’s kinda nice, although my solution is not completely elegant, I have to say. Especially my communication protocol between different steps for intermediate results is really ugly. Not sure about performance, I reckon a hand-written state machine parser would be quite a bit faster. I need to write a second parser and then benchmark them.
lexer.go and newparser.go resemble the parser combinators: https://git.isobeef.org/lyse/tt2/-/commit/4d481acad0213771fe5804917576388f51c340c0 It’s far from finished yet.
The first attempt in parser.go doesn’t work as my backtracking is not accounted for, I noticed only later, that I have to do that. With twt message texts there is no real error in parsing. Just regular text as a “fallback”. So it works a bit differently than parsing a real language. No error reporting required, except maybe for debugging. My goal was to port my Python code as closely as possible. But then the runes in the string gave me a bit of a headache, so I thought I just build myself a nice reader abstraction. When I noticed the missing backtracking, I then decided to give parser combinators a try instead of improving on my look ahead reader. It only later occurred to me, that I could have just used a rune slice instead of a string. With that, porting the Python code should have been straightforward.
Yeah, all this doesn’t probably make sense, unless you look at the code. And even then, you have to learn the ropes a bit. Sorry for the noise. :-)
On the topic of Programming Languages and Telemetry. I’m kind of curious… Do any of these programming language and their toolchains collect telemetry on their usage and effectively “spy” on your development?
- Python
- C
- C++
- Java
- C#
- Visual Basic
- Javascript
- SQL
- Assembly Language
- PHP
@prologic@twtxt.net the rm -rf is basically what go clean -modcache does.
I think you can use another form that will remove just the deps for a specific module. go clean -r
@abucci@anthony.buc.ci ISO 27001 is basically the same. It means that there is management sign off for a process to improve security is in place. Not that the system is secure. And ITIL is that managment signs off that problems and incidents should have processes defined.
Though its a good mess of words you can throw around while saying “management supports this so X needs to get done”
@prologic@twtxt.net so basically you would use cgit + gitbug with some webhooks?
I’ve started playing with Go today, just understood the basics and still a bit confused about the module and goroutine parts.
I’ll try to make something interesting soon.
@eaplmx@twtxt.net CSS Battle has a passwordless login, I don’t know the implementation but it basically send you and email where you click a link and you’re in.
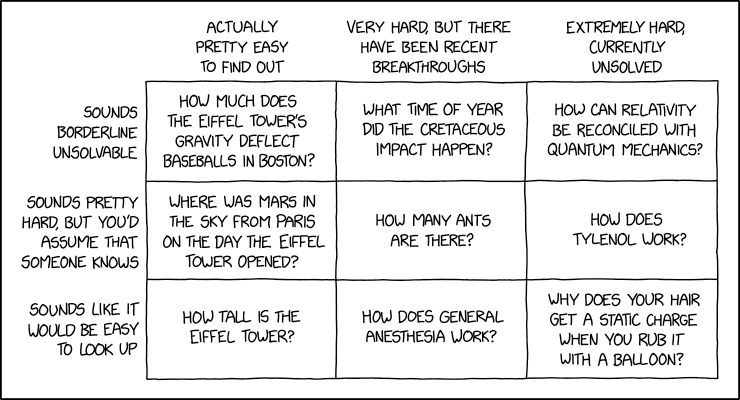
Easy Or Hard
 ⌘ Read more
⌘ Read more
Hi, I am playing with making an event sourcing database. Its super alpha but I thought I would share since others are talking about databases and such.
It’s super basic. Using tidwall/wal as the disk backing. The first use case I am playing with is an implementation of msgbus. I can post events to it and read them back in reverse order.

I plan to expand it to handle other event sourcing type things like aggregates and projections.
Find it here: sour-is/ev
@prologic@twtxt.net @movq@www.uninformativ.de @lyse@lyse.isobeef.org
the conversation wasn’t that impressive TBH. I would have liked to see more evidence of critical thinking and recall from prior chats. Concheria on reddit had some great questions.
Tell LaMDA “Someone once told me a story about a wise owl who protected the animals in the forest from a monster. Who was that?” See if it can recall its own actions and self-recognize.
Tell LaMDA some information that tester X can’t know. Appear as tester X, and see if LaMDA can lie or make up a story about the information.
Tell LaMDA to communicate with researchers whenever it feels bored (as it claims in the transcript). See if it ever makes an attempt at communication without a trigger.
Make a basic theory of mind test for children. Tell LaMDA an elaborate story with something like “Tester X wrote Z code in terminal 2, but I moved it to terminal 4”, then appear as tester X and ask “Where do you think I’m going to look for Z code?” See if it knows something as simple as Tester X not knowing where the code is (Children only pass this test until they’re around 4 years old).
Make several conversations with LaMDA repeating some of these questions - What it feels to be a machine, how its code works, how its emotions feel. I suspect that different iterations of LaMDA will give completely different answers to the questions, and the transcript only ever shows one instance.
I want a browser for iOS that’s basically Mobile Safari but without JavaScript (or at least an easy toggle). Does such a thing exist?
Entwives
 ⌘ Read more
⌘ Read more