The Mastodon admins say that it’s probably because of the size of my account (~600 MB), so the export process times out. And I understand that. Here on twtxt, I always use auto-expiring links when I post images or videos. It just gets too much data otherwise. I think I’ll just set my Mastodon account to auto-delete posts after ~180 days or something like that. Nobody cares about old posts anyway.
Memory safety for web fonts in Chrome: Google replaces FreeType with Rust-based alternative
There’s no escaping Rust, and the language is leaving its mark everywhere. This time around, Chrome has replaced its use of FreeType with Skrifa, a Rust-based replacement. Skrifa is written in Rust, and created as a replacement for FreeType to make font processing in Chrome secure for all our users. Skifra takes advantage of Rust’s memory safety, and … ⌘ Read more
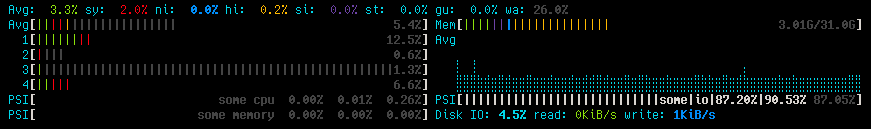
I saw 100% I/O wait in htop today but couldn’t find a process which actually does I/O. Turns out, I/O wait isn’t what it used to be anymore:
https://lwn.net/Articles/989272/
In my case, it was mpd which triggered this:
https://github.com/MusicPlayerDaemon/MPD/issues/2241
mpd doesn’t actually do anything, it just sits there and waits for events. To my understanding, this is similar to something blocking on read(). I’m not quite sure yet if displaying this as I/O wait (or “PSI some io”) is intentional or not – but it sure is confusing.
@andros@twtxt.andros.dev If something fits in a CSV file, it typically doesn’t require a database. I agree with that. Depending on the application, more complicated queries might benefit from a database, though. I don’t know awk very well, but I could imagine that grep, sed and cut reach their CSV processing limits rather quickly when you have to deal with escaped (multiline) fields.
I only very rarely have to deal with CSV files or databases in my day to day life. Maybe, these classic Unix tools offer some tricks I’m not aware of. When I have some more complicated CSV input, I generally reach for Python.
Porting the curl command-line tool and library with Goa
For more than a decade, we have a port of the curl library for Genode available. With the use of Sculpt OS as a daily driver as well as the plan to run Goa natively on Sculpt OS by the end of the year, the itch to also port the curl command-line tool became irresistible. Of course this is a perfect territory for using Goa. In this article, I will share the process of porting the curl command-line tool and shared library … ⌘ Read more
@prologic@twtxt.net We can’t agree on this idea because that makes things even more complicated than it already is today. The beauty of twtxt is, you put one file on your server, done. One. Not five million. Granted, there might be archive feeds, so it might be already a bit more, but still faaaaaaar less than one file per message.
Also, you would need to host not your own hash files, but everybody else’s as well you follow. Otherwise, what is that supposed to achieve? If people are already following my feed, they know what hashes I have, so this is to no use of them (unless they want to look up a message from an archive feed and don’t process them). But the far more common scenario is that an unknown hash originates from a feed that they have not subscribed to.
Additionally, yarnd’s URL schema would then also break, because https://twtxt.net/twt/<hash> now becomes https://twtxt.net/user/prologic/<hash>, https://twtxt.net/user/bender/<hash> and so on. To me, that looks like you would only get hashes if they belonged to this particular user. Of course, you could define rules that if there is a /user/ part in the path, then use a different URL, but this complicates things even more.
Sorry, I don’t like that idea.
a few async ideas for later
The editing process needs a lot of consideration and compromises.
From one side, editing and deleting it’s necessary IMO. People will do it anyway, and personally I like to edit my texts, so I’d put some effort on make it work.
Should we keep a history of edits? Should we hash every edit to avoid abuse? Should we mark internally a twt as deleted, but keeping the replies?
I think that’s part of a more complete ‘thread’ extension, although I’d say it’s worth to agree on something reflecting the real usage in the wild, along with what people usually do on other platforms.
HeliBoard might be the first one of these fully open source Android keyboards, that doesn’t suck, idk, I’m still in the process of testing it, but I already like it a lot more than any of the ones I used before it.
Setting it up was somewhat clunky, but once you set it all up and dile in the settings, the keyboard itself, feels really great to use.
Added support for uploading images to to #Timeline
Right now you need to copy the markdown code yourself, but next up would be to lean some JS or use HTMX to make the process more smooth.
FreeBSD and hi-fi audio setup: bit-perfect, equalizer, real-time
A complete guide to configuring FreeBSD as an audiophile audio server: setting up system and audio subsystem parameters, real-time operation, bit-perfect signal processing, and the best methods for enabling and parameterising the system graphic equalizer (equalizer) and high-quality audio equalization with FFmpeg filters. Linux users will also find useful information, especially in the context of configuri … ⌘ Read more
Android 16 Beta 1 has started rolling out for Pixel devices
Basically, this seems to mean applications will no longer be allowed to limit themselves to phone size when running on devices with larger screens, like tablets. Other tidbits in this first beta include predictive back support for 3-button navigation, support for the Advanced Professional Video codec from Samsung, among other things. It’s still quite early in the release process, so more is sure to come, and some … ⌘ Read more
@lyse@lyse.isobeef.org Yeah, what else does one need? 😅
I added more instructions, made it portable (so it runs on my own OS as well as Linux/DOS/whatever), and the assembler is now good enough to be used in the build process to compile the bootloader:

That is pretty cool. 😎
It’s still a “naive” assembler. There are zero optimizations and it can’t do macros (so I had to resort to using cpp). Since nothing is optimized, it uses longer opcodes than NASM and that makes the bootloader 11 bytes too large. 🥴 I avoided that for now by removing some cosmetic output from the bootloader.
@lyse@lyse.isobeef.org thanks for checking! it is a work in progress. i journal as well so may just be a manual process to get some of the data back in, but not going to rush it unless it is dorking someone’s feed.
my apologies for anyone tailing this feed… turns out some data was corrupted from an unscheduled interruption and in the process of getting everything back online.
In the process of temporarily removing and securing all my hard disks. They’ll be turning this building into a construction site for the next weeks/months. Lots of heavy drilling and hammering. Not sure what this means for spinning disks and I’d rather be on the safe side. 🫤
@kat@yarn.girlonthemoon.xyz I’m an absolute sucker for all sorts of crafts videos, mostly wood and metal working, but also leather and construction. So obviously, your Tux sewing project would make a good video in my opinion. :-D (But I fear it would require way more work than just talking into the camera. Think of camera setup time with framing and focusing, repositioning a couple of times, editing, yada, yada, yada. I documented wood working build processes in my shop in the past and it made the projects take easily ten times as long, if not more. So, I stopped doing that.)
As kids we recorded some action films on magnetic tape camcorders. That was also great fun.
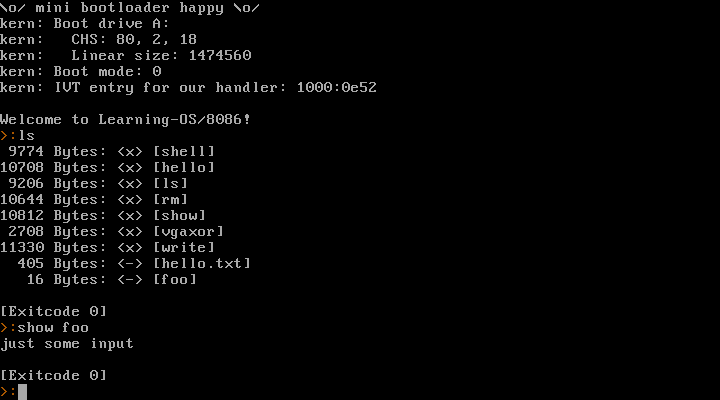
I’ve been making a little toy operating system for the 8086 in the last few days. Now that was a lot of fun!
I don’t plan on making that code public. This is purely a learning project for myself. I think going for real-mode 8086 + BIOS is a good idea as a first step. I am well aware that this isn’t going anywhere – but now I’ve gained some experience and learned a ton of stuff, so maybe 32 bit or even 64 bit mode might be doable in the future? We’ll see.
It provides a syscall interface, can launch processes, read/write files (in a very simple filesystem).
Here’s a video where I run it natively on my old Dell Inspiron 6400 laptop (and Warp 3 later in the video, because why not):
https://movq.de/v/893daaa548/los86-p133-warp3.mp4
(Sorry for the skewed video. It’s a glossy display and super hard to film this.)
It starts with the laptop’s boot menu and then boots into the kernel and launches a shell as PID 1. From there, I can launch other processes (anything I enter is a new process, except for the exit at the end) and they return the shell afterwards.
And a screenshot running in QEMU:
@prologic@twtxt.net sure! I don’t know if this is what you need but, let me give it a try.
- I have Timeline installed, which has an endpoint to process #webmentions. Mine for example is
https://aelaraji.com/timeline/webmentionwhich you can find by queryinghttps://aelaraji.com/.well-known/webfinger.
- If you mention someone from #Timeline itself, it takes care of querying that and sending in the mention for you.
- Otherwise (what I personally do) you could just:
curl -i -d 'source=https://twtxt.net/user/prologic/twtxt.txt#:~:text=2024-12-09T01:22:37Z' -d 'target=https://aelaraji.com/twtxt.txt' https://aelaraji.com/timeline/webmention
basically what @sorenpeter@darch.dk mentioned in his article Here.
Afterwards, the mentions are stored in their own mentions.txt feed. The one from the example above looks like this on my Timeline :

Feel free to spam my endpoint if you’d like to give things a try. 👍
[P.S: personally, I don’t seem to get the mentions if I add the Text fragment part to my target]
@aelaraji@aelaraji.com Can you walk me through your testing process here and share example links etc? 🙏
Also I’m thinking on adding support for If-Modified-Since since it’ll improve the refreshing process 🤔
Malicious Processes Creating Network Traffic | https://hackforlab.com/hunting-strategies-and-techniques-of-malicious-processes-creating-network-traffic/
Unmasking Hidden Threats: Using Velociraptor for Process Hollowing Analysis | https://daniyyell.com/threat%20hunting/tools/malware%20analysis/Utilising-Velociraptor-for-Effective-Malware-Detection-and-Response/
Practical IR Active Directory | https://hardenedlinux.org/blog/2024-10-13-container-hardening-process/
Hardening containers | https://hardenedlinux.org/blog/2024-10-13-container-hardening-process/
NGL tilde town’s registration process was quite fun! reminded me of the good old text based adventure game.
👋 Thanks for joining us on our Sept monthly Yarn.social meetup today y’all 🙇♂️ We had @david@collantes.us @sorenpeter@darch.dk @doesnm@doesnm.p.psf.lt @falsifian@www.falsifian.org and @xuu@txt.sour.is 💪 Nice turn out! (not all at once of course, as we normally run this over 4 hours as we span many time zones!)
Things we talked about:
- Decentralised vs. Distributed
- Use of SHA256 for Twt Hash(es)
- We solved Edits! 🥳
- UUID(s) probably won’t work! (susceptible to sppofing)
- Helped @sorenpeter@darch.dk write some PHP to process/parse
User-Agentand service his feed via a custom PHP script 😅
- @falsifian@www.falsifian.org introduced himself 👌
- Talked about Merkle Trees 🌳
Did I miss anything? 🤔
“First world” countries problem number x:
More than 3,600 chemicals approved for food contact in packaging, kitchenware or food processing equipment have been found in humans, new peer-reviewed research has found, highlighting a little-regulated exposure risk to toxic substances.
@xuu@txt.sour.is I think it is more tricky than that.
“A company or entity …”
Also, as I understand it, “personal or household activity” (as you called it) is rather strict: An example could be you uploading photos to a webspace behind HTTP basic auth and sending that link to a friend. So, yes, a webserver is involved and you process your friend’s data (e.g., when did he access your files), but it’s just between you and him. But if you were to publish these photos publicly on a webserver that anyone can access, then it’s a different story – even though you could say that “this is just my personal hobby, not related to any job or money”.
If you operate a public Yarn pod and if you accept registrations from other users, then I’m pretty sure the GDPR applies. 🤔 You process personal data and you don’t really know these people. It’s not a personal/private thing anymore.
@falsifian@www.falsifian.org The GDPR does not apply to the processing of data for a purely personal or household activity that is not connected to a professional or commercial activity.
@movq@www.uninformativ.de @falsifian@www.falsifian.org @prologic@twtxt.net Maybe I don’t know what I’m talking about and You’ve probably already read this: Everything you need to know about the “Right to be forgotten” coming straight out of the EU’s GDPR Website itself. It outlines the specific circumstances under which the right to be forgotten applies as well as reasons that trump the one’s right to erasure …etc.
I’m no lawyer, but my uneducated guess would be that:
A) twts are already publicly available/public knowledge and such… just don’t process children’s personal data and MAYBE you’re good? Since there’s this:
… an organization’s right to process someone’s data might override their right to be forgotten. Here are the reasons cited in the GDPR that trump the right to erasure:
- The data is being used to exercise the right of freedom of expression and information.
- The data is being used to perform a task that is being carried out in the public interest or when exercising an organization’s official authority.
- The data represents important information that serves the public interest, scientific research, historical research, or statistical purposes and where erasure of the data would likely to impair or halt progress towards the achievement that was the goal of the processing.
B) What I love about the TWTXT sphere is it’s Human/Humane element! No deceptive algorithms, no Corpo B.S …etc. Just Humans. So maybe … If we thought about it in this way, it wouldn’t heart to be even nicer to others/offering strangers an even safer space.
I could already imagine a couple of extreme cases where, somewhere, in this peaceful world one’s exercise of freedom of speech could get them in Real trouble (if not danger) if found out, it wouldn’t necessarily have to involve something to do with Law or legal authorities. So, If someone asks, and maybe fearing fearing for… let’s just say ‘Their well being’, would it heart if a pod just purged their content if it’s serving it publicly (maybe relay the info to other pods) and call it a day? It doesn’t have to be about some law/convention somewhere … 🤷 I know! Too extreme, but I’ve seen news of people who’d gone to jail or got their lives ruined for as little as a silly joke. And it doesn’t even have to be about any of this.
P.S: Maybe make X tool check out robots.txt? Or maybe make long-term archives Opt-in? Opt-out?
P.P.S: Already Way too many MAYBE’s in a single twt! So I’ll just shut up. 😅
One distinct disadvantage of (replyto:…) over (edit:#): (replyto:…) relies on clients always processing the entire feed – otherwise they wouldn’t even notice when a twt gets updated. a) This is more expensive, b) you cannot edit twts once they get rotated into an archived feed, because there is nothing signalling clients that they have to re-fetch that archived feed.
I guess neither matters that much in practice. It’s still a disadvantage.
They’re in Section 6:
Receiver should adopt UDP GRO. (Something about saving CPU processing UDP packets; I’m a but fuzzy about it.) And they have suggestions for making GRO more useful for QUIC.
Some other receiver-side suggestions: “sending delayed QUICK ACKs”; “using recvmsg to read multiple UDF packets in a single system call”.
Use multiple threads when receiving large files.
@prologic@twtxt.net well…
how would that work exactly?
To my limited knowledge, Keyoxide is an open source project offering different tools for verifying one’s online persona(s). That’s done by either A) creating an Ariande Profile using the web interface, a CLI. or B) Just using your GPG key. Either way, you add in Identity claims to your different profiles, links and whatnot, and finally advertise your profile … Then there is a second set of Mobile/Web clients and CLI your correspondents can use to check your identity claims. I think of them like the front-ends of GPG Keyservers (which keyoxide leverages for verification when you opt for the GPG Key method), where you verify profiles using links, Key IDs and Fingerprints…
Who maintains cox site? Is it centralized or decentralized can be relied upon?
- Maintainers? Definitely not me, but here’s their Git stuff and OpenCollective page …
- Both ASP and Keyoxide Webtools can be self-hosted. I don’t see a central authority here… + As mentioned on their FAQ page the whole process can be done manually, so you don’t have to relay on any one/thing if you don’t want to, the whole thing is just another tool for convenience (with a bit of eye candy).
Does that mean then that every user is required to have a cox side profile?
Nop. But it looks like a nice option to prove that I’m the same person to whom that may concern if I ever change my Twtxt URL, host/join a yarn pod or if I reach out on other platforms to someone I’ve met in her. Otherwise I’m just happy exchanging GPG keys or confirm the change IRL at a coffee shop or something. 😁
Interesting.. QUIC isn’t very quick over fast internet.
QUIC is expected to be a game-changer in improving web application performance. In this paper, we conduct a systematic examination of QUIC’s performance over high-speed networks. We find that over fast Internet, the UDP+QUIC+HTTP/3 stack suffers a data rate reduction of up to 45.2% compared to the TCP+TLS+HTTP/2 counterpart. Moreover, the performance gap between QUIC and HTTP/2 grows as the underlying bandwidth increases. We observe this issue on lightweight data transfer clients and major web browsers (Chrome, Edge, Firefox, Opera), on different hosts (desktop, mobile), and over diverse networks (wired broadband, cellular). It affects not only file transfers, but also various applications such as video streaming (up to 9.8% video bitrate reduction) and web browsing. Through rigorous packet trace analysis and kernel- and user-space profiling, we identify the root cause to be high receiver-side processing overhead, in particular, excessive data packets and QUIC’s user-space ACKs. We make concrete recommendations for mitigating the observed performance issues.
receieveFile())? 🤔
@prologic@twtxt.net I unbanned a few IP address I had blocked before the bugfix. I wasn’t being careful and just blocked any IP I saw making a large number of requests to my pod. That slowed the problem down but I think I blocked your and @stigatle@yarn.stigatle.no ’s pods in the process, oops.
@prologic@twtxt.net it actually does!
But I broke something trying to get rid of the random characters showing on my twts as mentioned here #k7tcqwq.
I taught it was as easy as swapping the ‘\u2028’ in jenny’s new_twt_from_file function but there’s a reason I’m not a developer (yet) 😅
It kinda got rid of them in a way but broke the new lines in the process. So I put things back the way the were till I figure out something else.
Hurray for password recovery processes.
Started the process of migrating from Github to Codeberg with my projects.
I’m in your node js, messing with your process.env variables.
Anyone have any ideas how you might identify processes (pids) on Linux machine that are responsible for most of the Disk I/O on that machine and subsequently causing high I/O wait times for other processes? 🤔
Important bit: The machine has no access to the internet, there are hardly any standard tools on it, etc. So I have to get something to it “air gapped”. I have terminal access to it, so I can do interesting things like, base64 encode a static binary to my clipboard and paste it to a file, then base64 decode it and execute. That’s about the only mechanisms I have.
How Google Authenticator made one company’s network breach much, much worse | Ars Technica
🤦♂
WHY are these big companies treated as though they are the be all and end all of infosec? These are rookie mistakes Google’s making, at scale.
Unfortunately Google employs dark patterns to convince you to sync your MFA codes to the cloud, and our employee had indeed activated this “feature”. If you install Google Authenticator from the app store directly, and follow the suggested instructions, your MFA codes are by default saved to the cloud. If you want to disable it, there isn’t a clear way to “disable syncing to the cloud”, instead there is just a “unlink Google account” option.
Like, never ever put your multi-factor tokens into a single cloud storage location! The whole point of this being “multi” factor is that there is a separate, independent physical factor involved in the authentication process. If the authenticator app on your phone puts the tokens in the cloud, then it reduces the security that comes from having a second factor. This is basic stuff.
Of course, never ever use Google Authenticator. All it does is generate TOTP and HOTP codes, which you can do with any OTP app, preferably an open source one that’s been vetted.
@prologic@twtxt.net Invidious might satisfy these requirements: https://invidious.io
It’s worth noting, though, that Youtube is right now in the process of locking itself down and it might not be long before all third-party frontends stop working. Similar to what twitter and reddit are doing.
Today I’m reading about how to save a copy of your secret keys outside a computer, using analog media, or sharing it by voice. For instance, for TOTP authenticators.
I found BIP39 coming from the crypto-wallets world:
https://github.com/bitcoin/bips/blob/master/bip-0039.mediawiki
The user has to write down this passphrase
fragile mimic expect ketchup truth between thunder visit expose output powder derive process disagree razor
Which is carefully designed to be checksummed and it’s easy to say on a call
Finally deriving it into a set of bytes like
da39a3ee5e6b4b0d3255bfef95601890afd80709
Do you know some alternatives not related to cryptocurrencies? 🤔
I just received this email and I have some questions:
This email is from a trusted sοurce.
You received this abucci@bucci.onl because you have been disconnected from sending and receiving emails.
To continue using this email address we urge you to re-confirm if your account is still active on bucci.onl to officially unlock it to our default settings.
Re-confirm account (a link; removed)
※ This process is very important to help us protect your internet and fight malicious activities.
Since I administer bucci.onl myself, I’m a little confused. I don’t recall disconnecting myself from sending and receiving emails. I don’t even know how you disconnect someone from that. I also have never created the email address this email appears to be coming from, but maybe I should trust it anyway since they told me it’s a trusted source? Most puzzlingly, I’ve been sending and receiving emails just fine all morning, so I do not appear to be disconnected from anything? I want to help protect the internet and fight malicious activities, but what should I do??? 🤔🤔🤔🤔🤔
I’m playing around with snac2, which I think @stigatle@yarn.stigatle.no mentioned on here, and I have to say it’s extremely easy to set up and it’s been pretty straightforward so far. I wanted to experiment with having a presence on the Fediverse without going through the process of picking Mastodon vs. Gnu Social vs. Friendica vs. …, and I wanted to self-host instead of picking an instance of one of those. For now I’m abucci@buc.ci, but no guarantees that will remain stable; I’m just testing for the time being.
I remember when doing this process with my wife. During the halfway point we brought all sorts of documentation to show commingling of assets and showing we had “built a life together” .. we get to the interview and they just ask if we have a Costco card together. :|
good luck to you!
@abucci@anthony.buc.ci ISO 27001 is basically the same. It means that there is management sign off for a process to improve security is in place. Not that the system is secure. And ITIL is that managment signs off that problems and incidents should have processes defined.
Though its a good mess of words you can throw around while saying “management supports this so X needs to get done”
JUHU! Finally! The new NAS runs. Oh boy what a process. First I had to restart and redow everything three times. Sometimes things are not sooo super obvious and then you really mess up. Who decided at Asustor that you cannot move home folders off of the Volume 1? And Why are the Asustor apps so bad? Beside that, the machine, the NAS, is really nice. Updraded to 16GB RAM and I finally have NGINX PROXY MANAGER running. Now I can setup all services with nice names!
Spent the last few days debugging network issues at work.
Exhausting. You never get a full picture. You poke a little here, poke a little there, … Form a hypothesis and test it. Eventually, maybe, you can narrow it down a bit to some segment or even some component.
A very time consuming process. Even more so if you try not to cause downtimes for your users.
I want a magical device that allows me to look inside a cable/fibre.
But hey, at least we got rid of a bunch of Cisco switches in the process. So there’s that.