Hello @bmallred@staystrong.run I hope you’re doing well.
I dunno if it’s normal, but it seems like I am unable to access your twtxt.tx file… 😅
I think @abucci@anthony.buc.ci and @stigatle@yarn.stigatle.no are running snac? I didn’t have a closer look at snac (no intention of running it), but if that is a relatively small daemon (maybe comparable to Yarn?) that gives you access to the whole world of ActivityPub, then, well, yeah … That’s tough to beat.
Yes, I am running snac on the same VPS where I run my yarn pod. I heard of it from @stigatle@yarn.stigatle.no, so blame him 😏 snac is written in C and is one simple executable, uses very little resources on the server, and stores everything in JSON files (no databases or other integrations; easy to save and migrate your data) . It’s definitely like yarn in that respect.
I haven’t been around yarn much lately. Part of that is that I’ve been very busy at work and home and only have a limited time to spend goofing off on a social network. Part of it is that I’m finding snac very useful: I’ve connected with friends I’d previously lost touch with, I’ve found useful work-related information, I’ve found colleagues to follow, and even found interesting conferences to attend. There’s a lot more going on over there.
I guess if I had to put it simply, I’d say I have limited time to play and there are more kids in the ActivityPub sandbox than this one. That’s not a ding on yarn–I like yarn and twtxt–I’m just time constrained.
Even AI coding machines will need to rotate their access credentials every 90 days.
in the matter of political voice in the US money is speech and therefore companies use their “free speech” to donate and gain access to politicians. Therefore companies are people. Thanks a lot “citizens united”
@lyse@lyse.isobeef.org its a hierarchy key value format. I designed it for the network peering tools i use.. I can grant access to different parts of the tree to other users.. kinda like directory permissions. a basic example of the format is:
@namespace
# multi
# line
# comment
root :value
# example space comment
@namespace.name space-tag
# attribute comments
attribute attr-tag :value for attribute
# attribute with multiple
# lines of values
foo :bar
:bin
:baz
repeated :value1
repeated :value2
each @ starts the definition of a namespace kinda like [name] in ini format. It can have comments that show up before. then each attribute is key :value and can have their own # comment lines.
Values can be multi line.. and also repeated..
the namespaces and values can also have little meta data tags added to them.

the service can define webhooks/mqtt topics to be notified when the configs are updated. That way it can deploy the changes out when they are updated.
Qnap’s Hybridmount feature makes it possible for me to access the files on OneDrive as if they were available from a local network drive on my Fedora PC. Pretty neat (when everything works).
Having fun with React - yet again. A large part of my job entails (re)learning technologies - luckily I have access to some good resources in the form of training- and tutorial sites, all provided by my employer.
I’m telling ya guys 😅 plex.tv had way better shit™, Get it installed on your own server, get access to free content + your own + whatever and no stupid tracking and bullshit 🤣
Anyone have any ideas how you might identify processes (pids) on Linux machine that are responsible for most of the Disk I/O on that machine and subsequently causing high I/O wait times for other processes? 🤔
Important bit: The machine has no access to the internet, there are hardly any standard tools on it, etc. So I have to get something to it “air gapped”. I have terminal access to it, so I can do interesting things like, base64 encode a static binary to my clipboard and paste it to a file, then base64 decode it and execute. That’s about the only mechanisms I have.
Pensée désagréable du jour: le protocole #gemini n’est pas écologique car il n’est pas accessible sur du vieux matériel à cause du TLS forcé. Servir des fichiers textes écrits en gemtext en #http est mieux dans ce cas
podman works with TLS. It does not have the "--docker" siwtch so you have to remove that and use the exact replacement commands that were in that github comment.
@prologic@twtxt.net what do you mean when you say “Docker API”? There are multiple possible meanings for that. podman conforms to some of Docker’s APIs and it’s unclear to me which one you say it’s not conforming to.
You just have to Google “podman Docker API” and you find stuff like this: https://www.redhat.com/sysadmin/podman-rest-api
What is Podman’s REST API?Podman’s REST API consists of two components:
- A Docker-compatible portion called Compat API
- A native portion called Libpod API that provides access to additional features not available in Docker, including pods
Or this: https://docs.podman.io/en/latest/markdown/podman-system-service.1.html
The REST API provided by podman system service is split into two parts: a compatibility layer offering support for the Docker v1.40 API, and a Podman-native Libpod layer.
Question to all you Gophers out there: How do you deal with custom errors that include more information and different kinds of matching them?
I started with a simple var ErrPermissionNotAllowed = errors.New("permission not allowed"). In my function I then wrap that using fmt.Errorf("%w: %v", ErrPermissionNotAllowed, failedPermissions). I can match this error using errors.Is(err, ErrPermissionNotAllowed). So far so good.
Now for display purposes I’d also like to access the individual permissions that could not be assigned. Parsing the error message is obviously not an option. So I thought, I create a custom error type, e.g. type PermissionNotAllowedError []Permission and give it some func (e PermissionNotAllowedError) Error() string { return fmt.Sprintf("permission not allowed: %v", e) }. My function would then return this error instead: PermissionNotAllowedError{failedPermissions}
At some layers I don’t care about the exact permissions that failed, but at others I do, at least when accessing them. A custom func (e PermissionNotAllowedError) Is(target err) bool could match both the general ErrPermissionNotAllowed as well as the PermissionNotAllowedError. Same with As(…). For testing purposes the PermissionNotAllowedError would then also try to match the included permissions, so assertions in tests would work nicely. But having two different errors for different matching seems not very elegant at all.
Did you ever encounter this scenario before? How did you address this? Is my thinking flawed?
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.
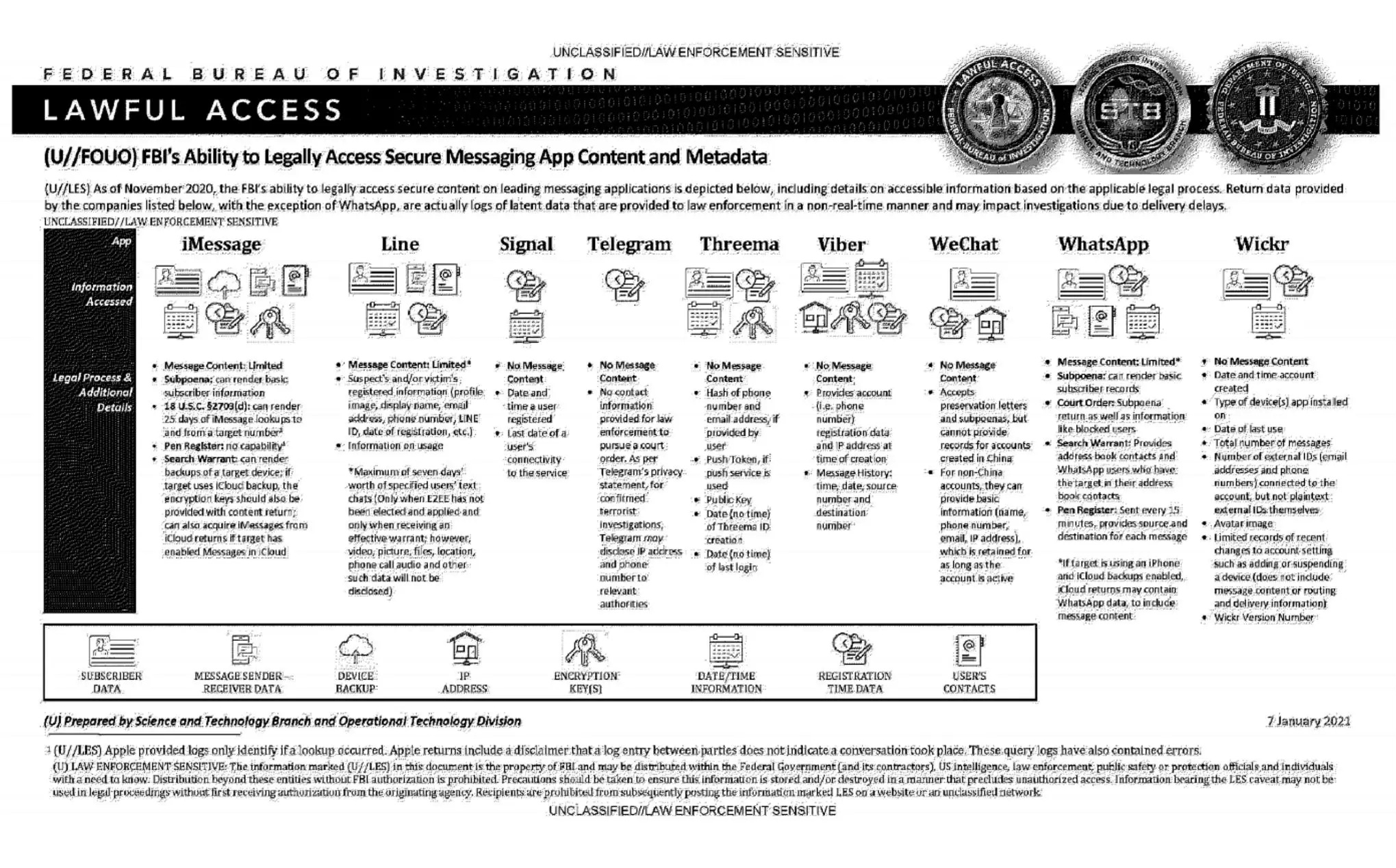
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
@prologic@twtxt.net I think those headsets were not particularly usable for things like web browsing because the resolution was too low, something like 1080p if I recall correctly. A very small screen at that resolution close to your eye is going to look grainy. You’d need 4k at least, I think, before you could realistically have text and stuff like that be zoomable and readable for low vision people. The hardware isn’t quite there yet, and the headsets that can do that kind of resolution are extremely expensive.
But yeah, even so I can imagine the metaverse wouldn’t be very helpful for low vision people as things stand today, even with higher resolution. I’ve played VR games and that was fine, but I’ve never tried to do work of any kind.
I guess where I’m coming from is that even though I’m low vision, I can work effectively on a modern OS because of the accessibility features. I also do a lot of crap like take pictures of things with my smartphone then zoom into the picture to see detail (like words on street signs) that my eyes can’t see normally. That feels very much like rudimentary augmented reality that an appropriately-designed headset could mostly automate. VR/AR/metaverse isn’t there yet, but it seems at least possible for the hardware and software to develop accessibility features that would make it workable for low vision people.
@stigatle@yarn.stigatle.no @prologic@twtxt.net @eldersnake@we.loveprivacy.club I love VR too, and I wonder a lot whether it can help people with accessibility challenges, like low vision.
But Meta’s approach from the beginning almost seemed like a joke? My first thought was “are they trolling us?” There’s open source metaverse software like Vircadia that looks better than Meta’s demos (avatars have legs in Vircadia, ffs) and can already do virtual co-working. Vircadia developers hold their meetings within Vircadia, and there are virtual whiteboards and walls where you can run video feeds, calendars and web browsers. What is Meta spending all that money doing, if their visuals look so weak, and their co-working affordances aren’t there?
On top of that, Meta didn’t seem to put any kind of effort into moderating the content. There are already stories of bad things happening in Horizon Worlds, like gangs forming and harassing people off of it. Imagine what that’d look like if 1 billion people were using it the way Meta says they want.
Then, there are plenty of technical challenges left, like people feeling motion sickness or disoriented after using a headset for a long period of time. I haven’t heard announcements from Meta that they’re working on these or have made any advances in these.
All around, it never sounded serious to me, despite how much money Meta seems to be throwing at it. For something with so much promise, and so many obvious challenges to attack first that Meta seems to be ignoring, what are they even doing?
They haven’t written the federation code yet. Its literally run on the staging instance. People are paying to access the alpha. Though if you want a code to see what all the fuss is about there are a few with invites around here.
There is a “right” way to make something like GitHub CoPilot, but Microsoft did not choose that way. They chose one of the most exploitative options available to them. For that reason, I hope they face significant consequences, though I doubt they will in the current climate. I also hope that CoPilot is shut down, though I’m pretty certain it will not be.
Other than access to the data behind it, Microsoft has nothing special that allows it to create something like CoPilot. The technology behind it has been around for at least a decade. There could be a “public” version of this same tool made by a cooperating group of people volunteering, “leasing”, or selling their source code into it. There could likewise be an ethically-created corporate version. Such a thing would give individual developers or organizations the choice to include their code in the tool, possibly for a fee if that’s something they want or require. The creators of the tool would have to acknowledge that they have suppliers–the people who create the code that makes their tool possible–instead of simply stealing what they need and pretending that’s fine.
This era we’re living through, with large companies stomping over all laws and regulations, blatantly stealing other people’s work for their own profit, cannot come to an end soon enough. It is destroying innovation, and we all suffer for that. Having one nifty tool like CoPilot that gives a bit of convenience is nowhere near worth the tremendous loss that Microsoft’s actions in this instace are creating for everyone.
I’m not super a fan of using json. I feel we could still use text as the medium. Maybe a modified version to fix any weakness.
What if instead of signing each twt individually we generated a merkle tree using the twt hashes? Then a signature of the root hash. This would ensure the full stream of twts are intact with a minimal overhead. With the added bonus of helping clients identify missing twts when syncing/gossiping.
Have two endpoints. One as the webfinger to link profile details and avatar like you posted. And the signature for the merkleroot twt. And the other a pageable stream of twts. Or individual twts/merkle branch to incrementally access twt feeds.
@xuu@txt.sour.is yeah, I know less about ISO27k (in part because you have to pay for access to the complete standards documents!!!), but I figured it was similar.
@mckinley@twtxt.net Thank you! I didn’t even know about signing and encrypting XML documents. Right, RSS is a little bit messy.
Unfortunately, the autodiscovery document in one of your linked resources does not exist anymore. What annoys me in Atom is the distinction between <id> and <link>. I always want my URL also to be my ID, so I have to duplicate that – unnecessarily in my opinion.
Also, never found a good explanation why I should add <link rel="self" … /> to my feeds. I just do, but I don’t understand why. The W3C Feed Validation Service says:
[…] This value is important in a number of subscription scenarios where often times the feed aggregator only has access to the content of the feed and not the location from which the feed was fetched.
This just sounds like a very questionable bandaid to bad software architecture. Why would the feed parser need access to the feed URL at this stage? And if so, why not just pass down the input source? Just doesn’t make sense to me.
Also, I just noticed that I reference the http://purl.org/rss/1.0/modules/syndication/ namespace, but don’t use it in most of my feeds. Gotta fix that. Must have copied that from my yfav feed without paying attention what I’m doing.
Your article made me reread the Atom spec and I found out, that I can omit the <author> in the <entry> when I specify a global <author> at <feed> level. Awesome! Will do that as well and thus reduce the feed size.
@abucci@anthony.buc.ci Its not better than a Cat5e. I have had two versions of the device. The old ones were only 200Mbps i didn’t have the MAC issue but its like using an old 10baseT. The newer model can support 1Gbps on each port for a total bandwidth of 2Gbps.. i typically would see 400-500Mbps from my Wifi6 router. I am not sure if it was some type of internal timeout or being confused by switching between different wifi access points and seeing the mac on different sides.
Right now I have my wifi connected directly with a cat6e this gets me just under my providers 1.3G downlink. the only thing faster is plugging in directly.
MoCA is a good option, they have 2.5G models in the same price range as the 1G Powerline models BUT, only if you have the coax in wall already.. which puts you in the same spot if you don’t. You are for sure going to have an outlet in every room of the house by code.
Huh… Nope.
HTTP/1.1 200 OK
Content-Length: 407
Content-Type: text/calendar
Access-Control-Allow-Origin: *
Access-Control-Expose-Headers: ETag
Permissions-Policy: interest-cohort=()
Content-Security-Policy: default-src 'none'; sandbox
Referrer-Policy: same-origin
Vary: Authorization
BEGIN:VCALENDAR
VERSION:2.0;2.0
PRODID:SandCal
CALSCALE:GREGORIAN
BEGIN:VEVENT
DTSTAMP:20220822T180903Z
UID:bb63bfbd-623e-4805-b11b-3181d96375e6
DTSTART;TZID=America/Chicago:20220827T000000
CREATED:20220822T180903Z
LAST-MODIFIED:20220822T180903Z
LOCATION:https://meet.jit.si/Yarn.social
SUMMARY:Yarn Call
RRULE:FREQ=WEEKLY
DTEND;TZID=America/Chicago:20220827T010000
END:VEVENT
END:VCALENDAR
New subscription plan for Apple Music: Voice Plan. Available for many countries. Using Siri to access songs. Meh.
created a little music streaming service for myself. uses the same access keys as /restricted-wiki/ friends welcome gemini://sunshinegardens.org/~xj9/arconite/playlists/
“People are taking the piss out of you everyday. They butt into your life, take a cheap shot at you and then disappear. They leer at you from tall buildings and make you feel small. They make flippant comments from buses that imply you’re not sexy enough and that all the fun is happening somewhere else. They are on TV making your girlfriend feel inadequate. They have access to the most sophisticated technology the world has ever seen and they bully you with it. They are The Advertisers and they are laughing at you. You, however, are forbidden to touch them. Trademarks, intellectual property rights and copyright law mean advertisers can say what they like wherever they like with total impunity. Fuck that. Any advert in a public space that gives you no choice whether you see it or not is yours. It’s yours to take, re-arrange and re-use. You can do whatever you like with it. Asking for permission is like asking to keep a rock someone just threw at your head. You owe the companies nothing. Less than nothing, you especially don’t owe them any courtesy. They owe you. They have re-arranged the world to put themselves in front of you. They never asked for your permission, don’t even start asking for theirs.” - Banksy
Words I cannot type rightly at the first attempt: testimonial, accessibility, successful
@vain@www.uninformativ.de I have seen it pop up on a few feeds around and adopted it into the new parser I built.
The format I have followed has been '# ' :whitespace: :key-name: :whitespace: '=' :whitespace: :value: keys can be repeated and accessed like an array of values.
@prologic@twtxt.net yep. it actually extracts everything at parse time. like mentions/tags/links/media. so they can be accessed and manipulated without additional parsing. it can then be output as MarkDown
On Kickstarter: SSHatellite A public-access shell server in space. https://www.kickstarter.com/projects/sshatellite/sshatellite