@movq@www.uninformativ.de, that would be a nice addition. :-) I would also love the ability to hide/not show the hash when reading twtxts (after all, that’s on the header on each “email”). Could that be added as a user configurable toggle?
@movq@www.uninformativ.de I don’t know if I’d want to discard the twts. I think what I’m looking for is a command “jenny -g https://host.org/twtxt.txt” to fetch just that one feed, even if it’s not in my follow list. I could wrap that in a shell script so that when I see a twt in reply to a feed I don’t follow, I can just tap a key and the feed will get added to my maildir. I guess the script would look for a mention at the start of a selected twt and call jenny -g on the feed.
@movq@www.uninformativ.de Is there a good way to get jenny to do a one-off fetch of a feed, for when you want to fill in missing parts of a thread? I just added @slashdot@feeds.twtxt.net to my private follow file just because @prologic@twtxt.net keeps responding to the feed :-P and I want to know what he’s commenting on even though I don’t want to see every new slashdot twt.
@prologic@twtxt.net Yeah, I’ve noticed that as well when I hacked around. That’s a very good addition, ta! :-)
Getting to this view felt suprisingly difficult, though. I always expected my feeds I follow in the “Feeds” tab. You won’t believe how many times I clicked on “Feeds” yesterday evening. :-D Adding at least a link to my following list on the “Feeds” page would help my learning resistence. But that’s something different.
Also, turns out that “My Feeds” is the list of feeds that I author myself, not the ones I have subscribed to. The naming is alright, I can see that it makes sense. It just was an initial surprise that came up.
@prologic@twtxt.net Fair enough! I just added some metadata.
@movq@www.uninformativ.de A good slogan for an ad: “Wwwwwwwwwwwwwwwwwwww! a hell of a bang for your buck!” 😂
@prologic@twtxt.net The old options are still valid, so “Show latest post per feed” should just be added as a 3th.
Radio advertisements slapping away sustained thought on the coffeeshop stereo. I’d like a real-life ad blocker.
@bender@twtxt.net Yeah I’ve been having this problem for quite sometime now. It boils down to Vi/Vim/NeoVim inserting those line breaks automatically when editing an .eml file (if I can remember the file extension correctly) … I think Jenny makes use of those. I had to delete them manually until I was told that the problem was fixed after I added the charset utf-8; to my nginx config file. I’ll try and fix this next…
# follow = dbucklin@www.davebucklin.com https://www.davebucklin.com/twtxt.txt?nick=dbucklin
I fixed it by adding (?<!\S) to the regex filter. But what is going on with the ?nick=dbucklin anyhow?
The wording can be more subtle like “This feed have not seen much activity within the last year” and maybe adding a UI like I did in timeline showing time ago for all feeds 
I agree that it good to clean up the Mastodon re-feeds, but it should also be okay for anyone to spin up a twtxt.txt just for syndicating they stuff from blog or what ever.
The “not receiving replies” could partly be fixed by implementing a working webmentions for twtxt.txt
@prologic@twtxt.net Thank
you! and here’s a twt with the said random characters, since I’ve been
cleaning them up manually, earlier before scp-ing my twtxt.txt file. And
maybe a screenshot of how things look in my editor? 
Those new lines are added automatically as I type (except for the ones
after the screenshot.
Anyone else look at YT and see ad where a scumbag comes out of the toiet and sprays frebreze all over his repulsive home
And now added #filter for replies too: 
Added support for #tag clouds and #search to timeline. Based on code from @dfaria.eu@dfaria.eu🙏
Live at: http://darch.dk/timeline/?profile=https://darch.dk/twtxt.txt
@lyse@lyse.isobeef.org its a hierarchy key value format. I designed it for the network peering tools i use.. I can grant access to different parts of the tree to other users.. kinda like directory permissions. a basic example of the format is:
@namespace
# multi
# line
# comment
root :value
# example space comment
@namespace.name space-tag
# attribute comments
attribute attr-tag :value for attribute
# attribute with multiple
# lines of values
foo :bar
:bin
:baz
repeated :value1
repeated :value2
each @ starts the definition of a namespace kinda like [name] in ini format. It can have comments that show up before. then each attribute is key :value and can have their own # comment lines.
Values can be multi line.. and also repeated..
the namespaces and values can also have little meta data tags added to them.

the service can define webhooks/mqtt topics to be notified when the configs are updated. That way it can deploy the changes out when they are updated.
@lyse@lyse.isobeef.org i made my own :D
I do prefer toml for the old school ini style with added support for object lists.
my second would be hjson or any other json with comments style.
Twtxt spec enhancement proposal thread 🧵
Adding attributes to individual twts similar to adding feed attributes in the heading comments.
https://git.mills.io/yarnsocial/go-lextwt/pulls/17
The basic use case would be for multilingual feeds where there is a default language and some twts will be written a different language.
As seen in the wild: https://eapl.mx/twtxt.txt
The attributes are formatted as [key=value]
They can show up in the twt anywhere it is not enclosed by another element such as codeblock or part of a markdown link.
Google Chrome Gains AI Features Including a Writing Helper
Google is adding new AI features to Chrome, including tools to organize browser tabs, customize themes, and assist users with writing online content such as reviews and forum posts.
The writing helper is similar to an AI-powered feature already offered in Google’s experimental search experience, SGE, which helps users draft emails in various tones and lengths. W … ⌘ Read more
Feels like my days of browsing YouTube for content are numbered. It’s only a matter of time before YouTube refuses to load for any browser with an ad blocker.
Bug Thread
 ⌘ Read more
⌘ Read more
I’ve added myself to the registries at registry.twtxt.org and twtxt.tilde.institute. I wonder if there’s a list of registries. #meta
Lo que aprendí mientras estaba en burn out. (Contado por un Software Engineer)
https://medium.com/@erikalmaraz_/lo-que-aprend%C3%AD-mientras-estaba-en-burn-out-contado-por-un-software-engineer-78b2eb4deda5
Typical Seating Chart
 ⌘ Read more
⌘ Read more
I have added a webmention endpoint to https://darch.dk using https://webmention.io - let see if it work from neotxt.dk to @sorenpeter@darch.dk
youtube ads, back button and forwards quickly seems to help (use keyboard shortcuts)
@lyse@lyse.isobeef.org I’m also on the e-mail wagon here. On http://darch.dk/timeline/conv/oe3howa I have added a “Comment via email” botten if uses are not logged in. This feature could be extend to other places in the various UIs. Like we already got the “Does not follow your” / “Follow you” on the profile page in yarnd, so this detection could be used to sugget the user to email that person, when mentioning them.
@prologic@twtxt.net Any of these work? https://gadgetstouse.com/blog/2023/05/15/bypass-ad-blockers-not-allowed-on-youtube/
So Youtube rea really cracking down on Ad-blockers. The new popup is a warning saying you can watch 3 videos before you can watch no more. Not sure for how long. I guess my options are a) wait for the ad-blockers to catch-up b) pay for Youtube c) Stop using Youtube.
I think I’m going with c) Stop using Youtube.
@prologic@twtxt.net I’ve even added the twthash message hash to my Twtxt bash CLI script so I can properly answer here.
@lyse@lyse.isobeef.org I wish more standardization around distributed issues and PRs within the repo ala git-bug was around for this. I see it has added some bridge tooling now.
This is some cool development for the go 1.22 standard http mux. Its adding the ability to have path vars and define methods for handlers. Also the errors are quite helpful if you have conflicting paths!
https://eli.thegreenplace.net/2023/better-http-server-routing-in-go-122/
@prologic@twtxt.net I have seen these screen shots. But have not yet seen them in actuality. I use ublockOrigin. Maybe it gets these too unlike adblock.
For android I have revanced.. The only place I get ads is on TV. I haven’t found a replacement there.
Oh okay, so Youtube is cracking down on “Ad Blockers”. 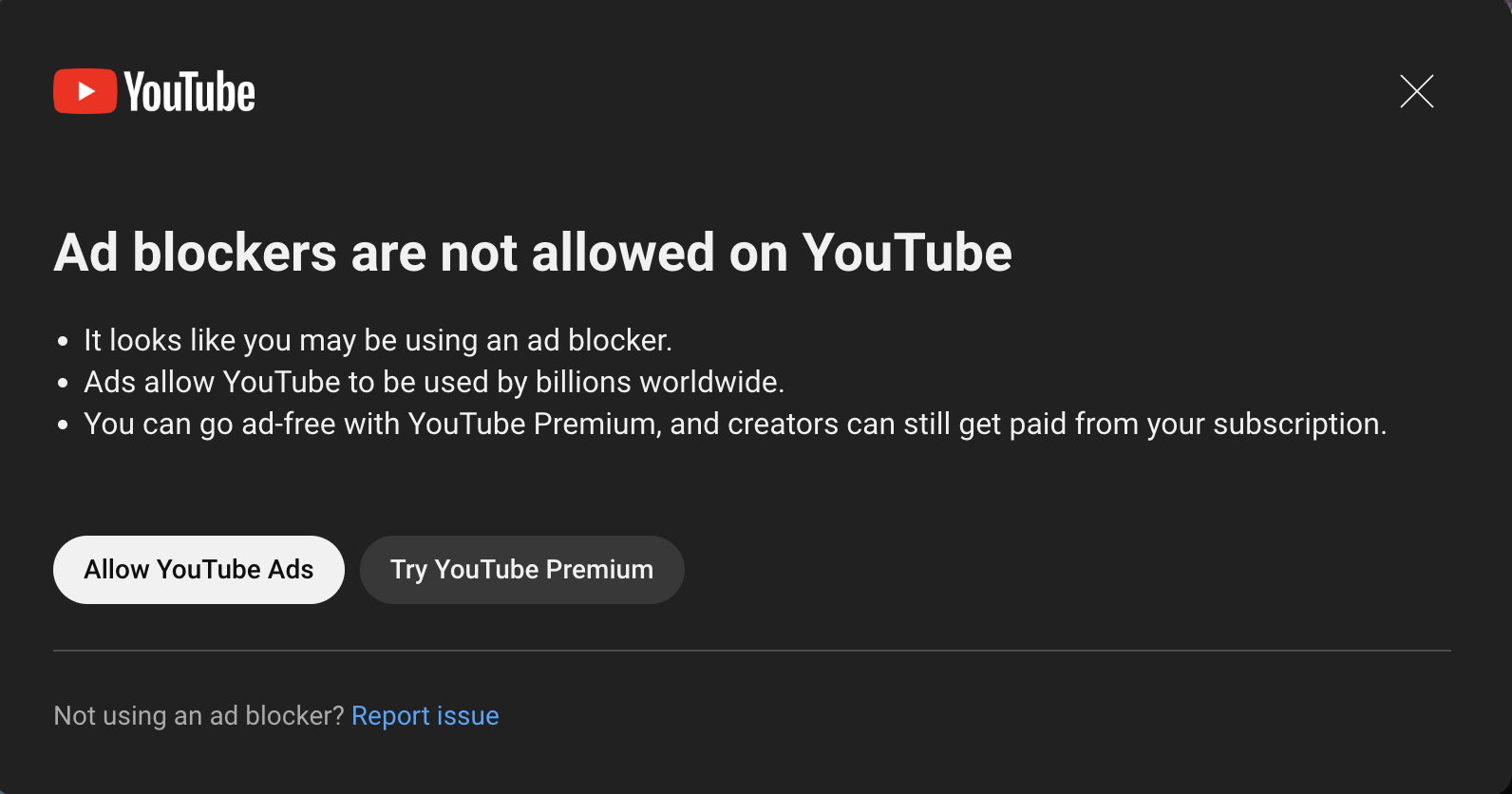 Rightio. 🤔 And paying for Youtube Premium costs $14/month?! 🤯
Rightio. 🤔 And paying for Youtube Premium costs $14/month?! 🤯  Get fucked 🤣 I guess I won’t be using Youtube anymore. #Youtube #Ads #Premium #Suck
Get fucked 🤣 I guess I won’t be using Youtube anymore. #Youtube #Ads #Premium #Suck
Ugh, ffs–the datasette project just added #ChatGPT garbage. Another seemingly nice piece of software and project that I need to stop using.
I guess I can be thankful they self-identify.
@prologic@twtxt.net @jmjl@tilde.green
It looks like there’s a podman issue for adding the context subcommand that docker has. Currently podman does not have this subcommand, although this comment has a translation to podman commands that are similar-ish.
It looks like that’s all you need to do to support podman right now! Though I’m not 100% sure the containers I tried really are running remotely. Details below.
I manually edited the shell script that cas.run add returns, changing all the docker commands to podman commands. Specifically, I put alias docker=podman at the top so the check for docker would pass, and then I replaced the last two lines of the script with these:
podman system connection add cas "host=tcp://cas.run..."
podman system connection default cas
(that … after cas.run is a bunch of connection-specific stuff)
I ran the script and it exited with no output. It did create a connection named “cas”, and made that the default. I’m not super steeped in how podman works but I believe that’s what you need to do to get podman to run containers remotely.
I ran some containers using podman and I think they are running remotely but I don’t know the right juju to verify. It looks right though!
This means you could probably make minor modifications to the generated shell script to support podman. Maybe when the check for docker fails, check for podman, and then later in the script use the podman equivalents to the docker context commands.
@prologic@twtxt.net aha, thank you, that got me unjammed.
Turns out I thought I had an SSH key set up in github, but github didn’t agree with me. So, I re-added the key.
I also had to modify the command slightly to:
ssh -p 2222 -i PRIVATE_GITHUB_KEY GITHUB_USERNAME@cas.run help
since I generate app-specific keypairs and need to specify that for ssh and I haven’t configured it to magically choose the key so I have to specify it in the command line.
Anyhow, that did it. Thanks!
# ssh -p 2222 cas.run help
The authenticity of host '[cas.run]:2222 ([139.180.180.214]:2222)' can't be established.
RSA key fingerprint is SHA256:i5txciMMbXu2fbB4w/vnElNSpasFcPP9fBp52+Avdbg.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[cas.run]:2222' (RSA) to the list of known hosts.
abucci@cas.run: Permission denied (publickey).
I’ve only been using snac/the fediverse for a few days and already I’ve had to mute somebody. I know I come on strongly with my opinions sometimes and some people don’t like that, but this person had already started going ad hominem (in my reading of it), and was using what felt to me like sketchy tactics to distract from the point I was trying to make and to shut down conversation. They were doing similar things to other people in the thread so rather than wait for it to get bad for me I just muted them. People get so weirdly defensive so fast when you disagree with something they said online. Not sure I fully understand that.
@prologic@twtxt.net wow! The place to go for whiteboard tech is mills.io.
That stinks about Excalidraw. they’ve been saying that (working on adding collab/self hosting) for over a year.
Li-Fi, light-based networking standard released
Today, the Institute of Electrical and Electronics Engineers (IEEE) has added 802.11bb as a standard for light-based wireless communications. The publishing of the standard has been welcomed by global Li-Fi businesses, as it will help speed the rollout and adoption of the data-transmission technology standard. Where Li-Fi shines (pun intended) is not just in its purported speeds as fast as 224 GB/s. Fraunhofer’s Dominic Schulz points ou … ⌘ Read more
With Youtube testing a “three strikes and you’re out” policy against people who use ad blockers, I’m also wondering whether Web 2.0 is effectively walled off and I should just give up on it entirely and look elsewhere for information and entertainment.
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.
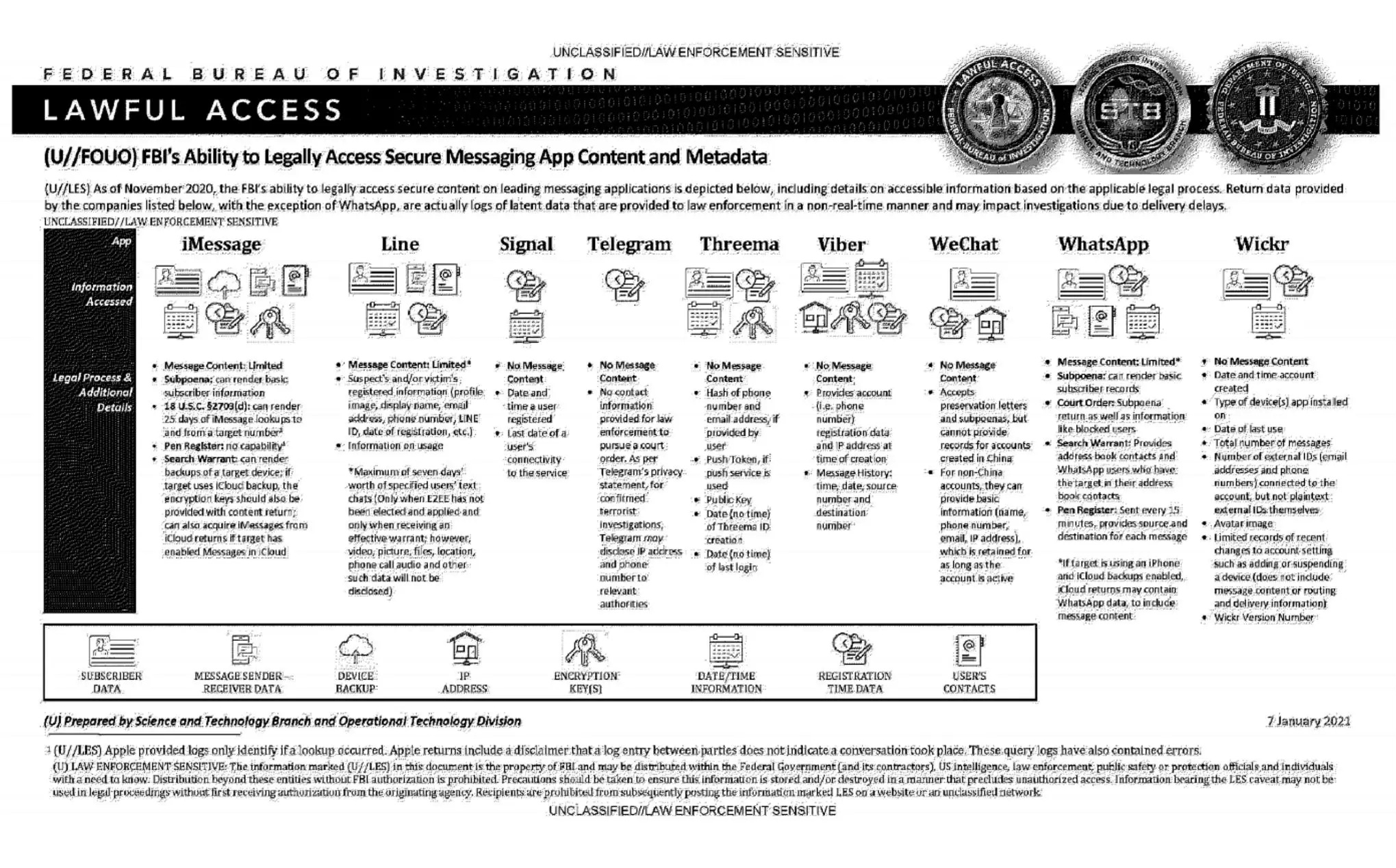
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
@prologic@twtxt.net I said nothing about an international violent response. You added that 🤔
If someone punches you in the face over and over again, you don’t stand there and take it to avoid “begetting violence”. You stop them from punching you, and do your best to ensure they never punch you again. That’s not “violence begets violence”. That’s rationality.
And a new page where a new link is added every hour (in EN, ES and FR)
https://eapl.mx/links/
My desktop computer developed a really annoying vibration-induced buzzing sound a few months ago after I added some hard drives to it. It was one of these where it’d be more or less quiet, and then all of a sudden a buzzing would start. If you tapped the case, it often made the buzzing stop.
One by one I went through my components, and the day before yesterday I finally identified the guilty party, one particular HDD. Currently I have the case open and a piece of cardboard jammed under the drive in its tray. The computer has not buzzed since I did that, so it looks to me like securing that drive better will finally end this madness-inducing sound.
Wild that it takes so long to track down something like this and figure out what to do about it.
I was listening to an O’Reilly hosted event where they had the CEO of GitHub, Thomas Dohmke, talking about CoPilot. I asked about biased systems and copyright problems. He, Thomas Dohmke, said, that in the next iteration they will show name, repo and licence information next to the code snippets you see in CoPilot. This should give a bit more transparency. The developer still has to decide to adhere to the licence. On the other hand, I have to say he is right about the fact, that probably every one of us has used a code snippet from stack overflow (where 99% no licence or copyright is mentioned) or GitHub repos or some tutorial website without mentioning where the code came from. Of course, CoPilot has trained with a lot of code from public repos. It is a more or less a much faster and better search engine that the existing tools have been because how much code has been used from public GitHub repos without adding the source to code you pasted it into?
Quite predictably, the introduction of Chat GPT, has led to even more browser bloat. 🎉
Also since I’m already bringing up opera - I have genuinely no idea, what their dev team is smoking, as all their additions this year, have been this desperate:

From some cashback scam and TikTok integration…
…all the way to some “lonely men bait” and adding NFTs - a full year, after everyone stopped caring.
I’m not super a fan of using json. I feel we could still use text as the medium. Maybe a modified version to fix any weakness.
What if instead of signing each twt individually we generated a merkle tree using the twt hashes? Then a signature of the root hash. This would ensure the full stream of twts are intact with a minimal overhead. With the added bonus of helping clients identify missing twts when syncing/gossiping.
Have two endpoints. One as the webfinger to link profile details and avatar like you posted. And the signature for the merkleroot twt. And the other a pageable stream of twts. Or individual twts/merkle branch to incrementally access twt feeds.
@prologic@twtxt.net I get the worry of privacy. But I think there is some value in the data being collected. Do I think that Russ is up there scheming new ways to discover what packages you use in internal projects for targeting ads?? Probably not.
Go has always been driven by usage data. Look at modules. There was need for having repeatable builds so various package tool chains were made and evolved into what we have today. Generics took time and seeing pain points where they would provide value. They weren’t done just so it could be checked off on a box of features. Some languages seem to do that to the extreme.
Whenever changes are made to the language there are extensive searches across public modules for where the change might cause issues or could be improved with the change. The fs embed and strings.Cut come to mind.
I think its good that the language maintainers are using what metrics they have to guide where to focus time and energy. Some of the other languages could use it. So time and effort isn’t wasted in maintaining something that has little impact.
The economics of the “spying” are to improve the product and ecosystem. Is it “spying” when a municipality uses water usage metrics in neighborhoods to forecast need of new water projects? Or is it to discover your shower habits for nefarious reasons?